Cross-domain solutions (CDSs) are a vital component when it comes to the security of our most important digital-based…
Mercury SystemsApril 16, 2025
Read More
Blog
Electromagnetic spectrum superiority in modern defenseThe electromagnetic spectrum is an integral part of our daily lives, yet its complexity often goes unnoticed. In defense, the…
Mercury SystemsNovember 25, 2024
Read MoreVodcast
Delivering innovative technologies to support Army modernization and transformation effortsDr. Eric Gans, Mercury's business development director for advanced technology, shares how Mercury supports the U.S. Army…
Mercury SystemsNovember 8, 2024
Read More
Vodcast
Delivering processing innovation for the air and space domainsMercury’s chief operating officer, Roger Wells, sat down for an interview with Air & Space Forces Magazine to discuss the…
Mercury SystemsSeptember 13, 2024
Read MoreFeatured
Blog
CHIPS Part 1: National security and the state of domestic chip manufacturingThe international chip-supply situation is putting U.S. security at risk and driving the need for the ...
March 8, 2023
Read MoreBlogs & Podcasts

“Volunteers do not necessarily have the time; they just have the heart.”– Elizabeth Andrew On a rainy March day, 5 Mercury employees based in Andover trekked into Boston to participate in our first Boston City Year volunteer event.
Mercury SystemsApril 1, 2019
Read More
In military environments, seconds can be the difference between life or death and mission success or failure. A soldier in hostile territory needs their mobile system to rapidly process sensor data to accurately analyze threats and take action. Intelligent sensor systems using artificial intelligence (AI) to make automatic critical decisions without human intervention rely on […]
Jennifer KeenanMarch 14, 2019
Read More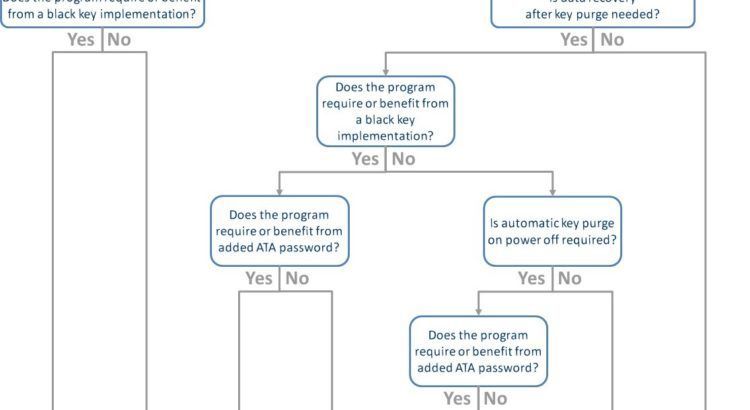
In my prior three posts, I provided an overview of encryption key fundamentals and the various encryption key mode strategies that can be implemented in a Mercury secure SSD. If you did not read those, stop everything and go back to them now!
Jennifer KeenanMarch 8, 2019
Read More
Cloud, Fog and Edge Computing for Defense Applications.
Shaza KhanMarch 5, 2019
Read More