Maintain data integrity and safeguard IP at the edge
Our RTBX05 rugged BuiltSECURE™ server delivers uncompromised security and protects critical data and technology from loss or compromise. To meet a variety of system requirements, the rugged BuiltSECURE servers feature a trusted motherboard with with dual Intel® Xeon® E5-2600 v4 processors, built-in security features, up to 120 TB of storage, high speed I/O and multiple expansion slots.

Stay Ahead of Threats
Rugged Trusted BuiltSECURE Servers mitigate reverse engineering and safeguard against threats with features from our proven technology suite which includes:
- Access control
- Non-volatile memory-write protection
- Sanitization
- Physical protection mechanisms
- Sensors
- Key management
- Data-at-rest protection
- Secure firmware management
- Cryptographic offload engine capabilities
Thank you! We have received your message and will be in touch with you shortly.
Lower Your Total Cost of Ownership
Systems exposed to classified information in the field must be physically guarded or properly sanitized. Our built-in board volatility features ensure no classified data is unintentionally stored on the hardware, avoiding the need for expensive handling.
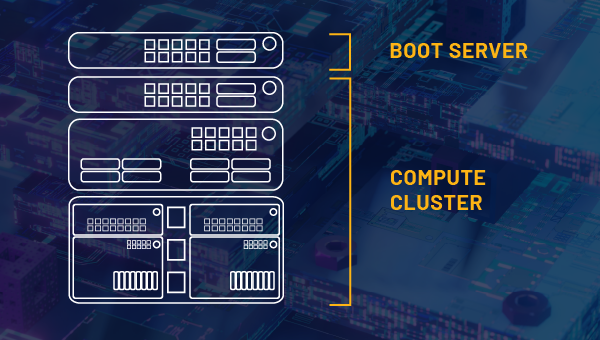
Secure Your Server Cluster
When configured as a boot server, BuiltSECURE technology ensures only authorized personnel can modify the cluster. Built-in cryptography and physical security delivers assurance and maintains data integrity even when the stack is offline or remotely accessed, making it ideal for edge applications.


