Thank you! We have received your message and will be in touch with you shortly.

Operate Confidently
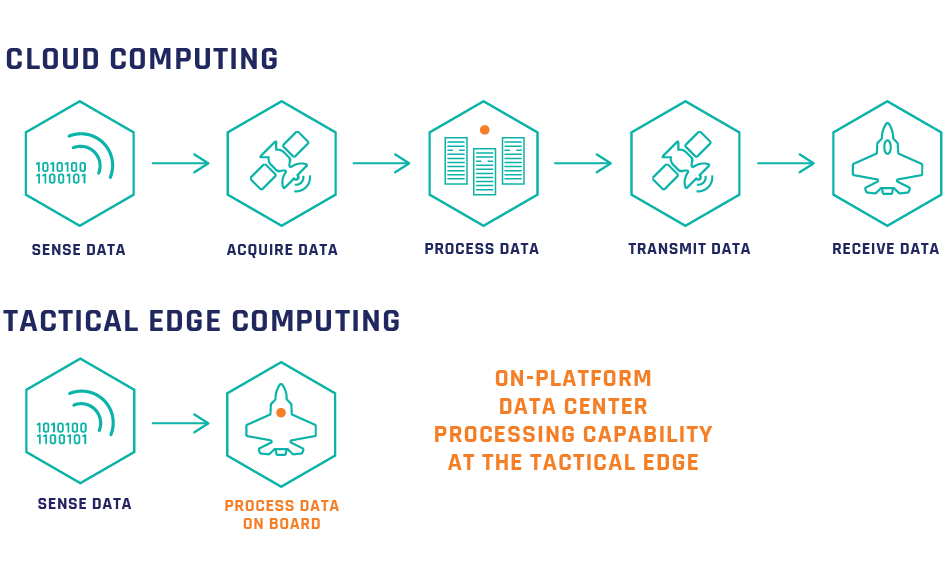
Contested environments present additional challenges for applications operating at the edge. Robust data confidentiality/integrity hardware protections are needed to keep critical mission data secure. Our combination of highly advanced physical security features, complex data processing capability and SWaP optimization efficiently delivers secure, mission-critical insight – anywhere – even when a host system has been compromised.
Interoperable, Scalable and Refreshable
Deploy faster by building your next secure processing solution with EnsembleSeries processing modules. Our OpenVPX modules are based on open architecture standards including Sensor Open System Architecture (SOSA) for interoperability, scalability and rapid modernization. Drive affordability and performance while lowering your program risk by using an architecture that evolves at the speed of technology, follows Intel’s technology roadmap and leverages cutting-edge commercially developed hardware, software and IP.
TRUSTED MANUFACTURING
Security Without Compromise
Minimize your risk to back doors, counterfeits and Trojans. BuiltSECURE™ products are designed and manufactured in trusted IPC-1791-certified and DMEA-accredited facilities mitigating opportunities for tampering.
Field-Proven Boards
Maximize performance and scalability
Integrate, tailor and optimize your unique subsystem to accelerate mission-critical applications using Mercury’s highly configurable SBCs with Intel single- and multicore processors and multiple mezzanine sites.
RELATED PRODUCTS

Embedded Processing Subsystems
Pre-integrated, SWaP-optimized, customizable OpenVPX multifunction subsystems with program support services, security

Multiprocessing
6U OpenVPX multifunction boards powered by server-class Intel Xeon Scalable processing technology

Networking
High-bandwidth network switch boards for unrestricted connectivity within OpenVPX systems

SecRun Integrated Security Platform
Runtime cryptography for ASIC and FGPA-based systems
DISCOVER MORE
Universal Storage for Fast Access to All Data at the Edge Webinar, Military Embedded Systems
Join VAST Data Federal and Mercury to learn more about an affordable ruggedized all-flash...
Mercury System's Embedded Advantage: Faster and Better on the Edge
Mercury Systems' chief operating officer, Roger Wells, sat down for an interview with Air & Space...
Webinar: Advantages and Trade Offs with Direct RF for Next Generation Embedded Systems
Direct RF technology is setting a new standard for performance with modern wireless communication...
This is not a drill: Preparing for a severe cyber storm
Designing post-quantum cryptography (PQC) is much more than just implementing an algorithm. You need...

